Net Trust
This page is no longer maintained. Please go to current publications, research, or overview.
Researchers:
L Jean Camp, Alla Genkina,
| Lead Developers | Team Members |
| Alex Tsow Camilo Viecco | Brandon Stephens, Allan Friedman, Zack Zimmerman (A NSF REU scholar) |
Resources:
Code
Code is available using Google Projects, http://code.google.com/p/nettrust/. Please note that we will not know who you are if you download the code nd use it, so feel free to contact us with suggestions. Because we cannot contact you as a user to ask for them
There is a daily build with an installer available at the IU site http://nettrust0.ucs.indiana.edu/. The code is under an Apache license. Please feel free to join and create social networks. Because this code changes every week, please look at code page for status. To install, run install under the Toolbar directory and then open the resulting xpi file with Mozilla Firefox. Firefox will then install Net Trust. You will need to create your own nyms and social networks.
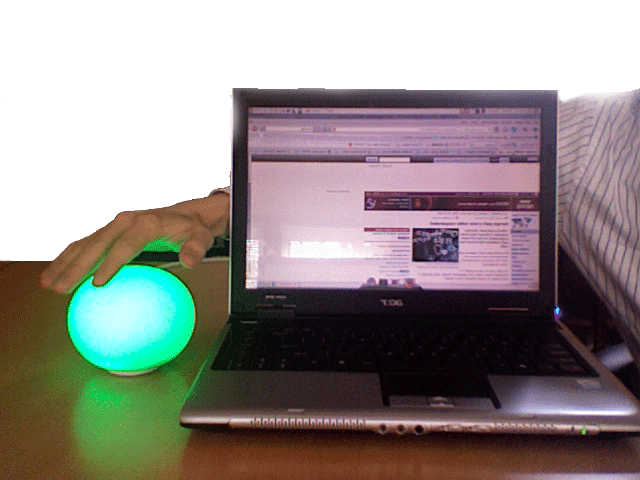
Views of the Ambient Interface to Net Trust
 |  |
|---|
Papers
NEW The Ambient Trust Orb, a Net Trust interface for the non-technical individual. Slides and PhotosComing Soon: IBM Systems Journal on architecture
A user study of usability and trust behaviors
A description of the architecture with a focus on the complementary nature of privacy and security in this design.
A presentation that includes current screen shots, as of Monday July 16.
An initial user study that illustrates that Net Trust both increases and decreases trust behavior depending on the information in the toolbar.
A presentation illustrating the theory and protocol alternatives.
A workshop paper of why Net Trust will work in economic terms. Net trust provides signaling in an economic sense to allow individuals to make informed choices.
A draft paper explaining the social theory and the first generation interface in detail.
A modeling paper describing the conditions under which a peer-based system would function. This paper by Allan Friedman uses agent-based modeling to evaluate the potential of the idea.
Theory
Individuals are socialized to trust, and trust is a necessary enabler of e-commerce. The human element is the core of confidence scams, so any solution must have this element at its core.
Scammers, such as phishers and purveyors of 419 fraud, are abusing trust on the Internet. All solutions to date, such as centralized trust authorities, have failed. Net Trust is the solution - trust technologies grounded in human behavior. What is unique about NetTrust?
NetTrust uses ratings from a users' social network and from user-selected third parties. NetTrust informs user decisions, as opposed to altering security settings. The end user selects a set of roles, i.e. psuedonyms. When the user leaves each web site, the user chooses to share information or not about his history. The user sends out a flow of information using RSS, but that feed is not associated with an identifiable user.
Impersonation is easy on the network because web sites are presented without social, geographical or physical context. A myriad of technical solutions have been proposed to solve the problem of people judging a web site, but none of them have been based on sound social as well as technical foundations. NetTrust allows users to share their own information, and to determine if a web site is as its claimed.
Centralized trust authorities have proven unreliable (e.g., TRUSTe) and trust seals are easy to copy. In fact, multiple mechanisms which create a single trusted third party have failed to resolve impersonation problems, in part because single trusted third parties themselves lack context. Phishing is a profitable and growing segment of impersonation crime, despite the ubiquity of security and authentication in the form of SSL.
There are not widespread usable heuristics that guide people on how to extend trust on the Internet. The technical solution has been to develop trusted third parties that send out binary signals: trust or don't trust. This solution has failed, as illustrated by the magnitude of Internet scams. Individuals are socialized to trust, and trust is a necessary enabler of e-commerce. The human element is the core of confidence scams, so any solution must have this element at its core.
The core of this system is a trust mechanism that is grounded in human trust behaviors. The range of extant security technologies can solve the problems of impersonation in a technical sense; however these have failed in the larger commercial and social context. People can make subtle distinctions based on context. People do trust the opinions of their own social networks, and may select their own mediators of trust in different domains (e.g., Consumer Union). Therefore, we are developing a socio-technical solution which uses social networks to re-embed social information on-line that is imbued by geography and physical design off-line.
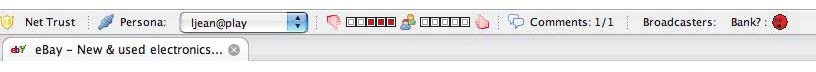
A toolbar presentation of a web page that is widely agreed not to be trustworthy.
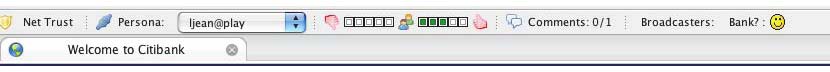
A toolbar presentation of a web page that is widely agreed to be trustworthy.
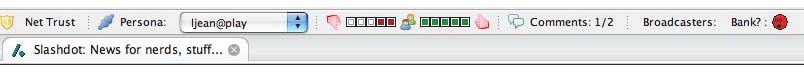
A toolbar presentation of a web page for which there is no agreement.
The system builds upon three features that cannot be altered without having read and write control of a users' machine: user history, user preferences, and user social network. In work with Cathleen Blythe & Helen Nissenbaum, we noted that assumptions in the design of computer security mechanisms contrast with the findings HCI and psychological studies.(See the paper as presented at Financial Cryptography). The design is based on human trust behaviors.
The system builds upon social networks and the trust embedded in those networks to evaluate sites using both informal and formal mechanisms. (The characteristics of the underlying reputation network are described in the draft paper linked below.) Essentially this system adds context to the browsing experience in order to provide explicit trust information. This application does not offer a trust decision for the user, but provides information to enable the user to make that decision. The system will do this by combining social bookmarking, reputation systems, and self-signed certificates. The project consists of two parts: interaction design and reputation system design. The project builds upon reputation systems, social browsing, friend-of-a-friend research, and existing tools for confidentiality and authentication.